Cloud DDoS Protection: How to Mitigate All Risks
Before answering your question about how to protect against DDoS, you should understand what a DDoS attack is and what types of such attacks exist.
What is a DDoS (Distributed Denial-of-Service) attack?
It’s an attempt to flood a network, system, or application with more traffic, connections, or requests than it can handle. This can have disastrous effects for businesses and other types of organizations, such as governments.
For major websites and applications, even a few seconds of downtime can result in a significant loss of revenue and a disruption of services. DDoS is a non-intrusive attack which means the attacker doesn’t need admin access to your site or application to run it and this traffic can look normal at first.
A DDoS attack is launched from numerous compromised devices and also from several different networks, often distributed over the world in what is called a botnet. A botnet refers to a group of computers that have been infected by malicious software (malware). This is the main distinction from the Denial of Service (DoS) attack, which uses a single device (one network).
Why do DDoS attacks exist?
DDoS attacks can be launched for various reasons ranging from activism to state-sponsored disruption, with many attacks being carried out simply for profit. Hiring services online for DDoS attacks is relatively inexpensive, especially in relation to the amount of damage they can cause.
Why is DDoS a problem and what does it impact?
- Availability of your applications or websites: Attacks can last for hours or even days and block your users from normal usage of your applications.
- The financial impact on your business: Lost revenue, increased expenses on IT infrastructure provisioning.
- Security of your data: DDoS attacks can lead to data losses.
- The reputation of your applications: The name of your brand takes damage and loses credibility.
What are the common types of DDoS attacks?
DDoS attacks can be mainly divided by which layer of the OSI model they attack.

- Application-Layer Attacks (layer 7) - HTTP floods, DNS query floods: Composed of requests (HTTP GETs and DNS queries are popular) that are designed to consume application resources (memory, CPU, bandwidth). An example is an attacker who continuously uses a website functionality (submitting a contact form or any API requests) where he knows that it causes database and application processing so that the underlying web service is busy with malicious requests and can’t deliver to other users anymore. The main difficulty when trying to mitigate an Application - Layer attack is distinguishing between normal and malicious traffic.
- State-Exhaustion Attacks (layer 4) - SYN Flood: Consume the TCP connection state tables present in many network infrastructure and security devices, including routers, firewalls, and load-balancers, as well as the application servers themselves. The attacker quickly initiates a connection to a server without finalizing the connection. These attacks can block access for legitimate users or make security devices inoperative, sometimes even leaving defenses wide-open to data exfiltration. This type of a DDoS attack was used in the DYN attack in 2016 which resulted in major websites like Amazon, Twitter, Github, and others becoming unavailable.
- Volumetric Attacks (layer 3): Also referred to as Network floods, and includes UDP floods (UDP reflection attacks) and ICMP floods. This type of attack occurs when a network is overwhelmed by a large amount of malicious traffic, causing your applications or services to become unavailable to users. Typically, this type of attack is described in 100s of Gbps, but some of the recent attacks have scaled to over 1Tbps.
Stormit solutions for a DDoS attack mitigation
When you become a Stormit customer, our experts become an extension of your team, designing and supporting a secure AWS infrastructure for your needs.
We offer AWS Edge Services (Amazon CloudFront, AWS WAF, Amazon Route 53 and AWS Shield) in our special bundles, so you can leverage DDoS protection and overall security for your applications.
The pricing of these bundles is mainly based on your monthly data transfer and we provide special pricing for organizations transferring as little as 1 TB of data per month.

You can read more about our offers here:CDN Security
Approaches to DDoS attacks mitigation in general
At this point, you should understand that there is no easy way to avoid a DDoS attack, but there are some techniques to mitigate against such attacks:
- Continuous monitoring of capacity (system CPU load, inbound traffic load etc.), traffic type, and any critical infrastructure and service (e.g. firewalls etc.).
- Segmentation of internal to external networks and of any network containing critical systems.
- Use cloud-based hosting from a major cloud service provider with high bandwidth and CDN (content delivery network) that cache websites or application data. If you use a Content Delivery Network, avoid disclosing the IP address of the origin web server, and use a firewall to ensure that only the CDN service can access this web server.
- Implement monitoring of availability with real-time alerts to detect DDoS attacks and measure their impact.
Some more specific techniques on how to mitigate DDoS attacks:
- Plan scale of your infrastructure thoroughly: the majority of DDoS attacks are based on large volume and trying to exhaust the capacity of your resources (bandwidth, server). For bandwidth make sure your hosting provider provides reliable internet connectivity that allows you to handle large volumes of traffic. For servers, it’s important that you can quickly scale up or down on your computation resources or that you have enough resources from the start. It is also a good idea to use load balancers to shift loads between servers to prevent overloading one of the servers.
- Reduce surface area of your network: Create minimized “surface” area that can be attacked and build protections in a single place. Your application or resources should block any communication from any ports, protocols or applications from unexpected sources. You can use firewalls or Access Control Lists (ACLs) to control what traffic reaches your applications. You can also place your resources behind Content Delivery Network (CDN) or load balancer.
Do you have any questions regarding DDoS protection of your application or infrastructure? Contact us and get a free consultation.Contact Us
Amazon Web Services (AWS) Cloud DDoS mitigation
Two ways to use AWS services for DDoS attacks mitigation:
- You already use AWS services (EC2, S3, RDS, etc..) and want to know more about services they offer for DDoS mitigation.
- You have some other solution (on-premises, other cloud service provider) and want to know more about how to mitigate DDoS attacks by using AWS services. A simple example of using AWS services for mitigation of DDoS with a server outside of AWS is a situation where, for example, for regulatory reasons you are not able to migrate your data or whole application to AWS servers, but you can leverage AWS infrastructure for DDoS attacks mitigation. This can be achieved by using AWS services that operate from edge locations.
AWS services for DDoS mitigation
First, it’s good to see some architecture examples to help you understand the best way to mitigate and protect your application against possible DDoS attacks.
This reference architecture includes several AWS Edge Services that can help you improve your web application’s resiliency against DDoS attacks, but also secure your application and infrastructure in other ways. This architecture is intended for those who use only AWS services.
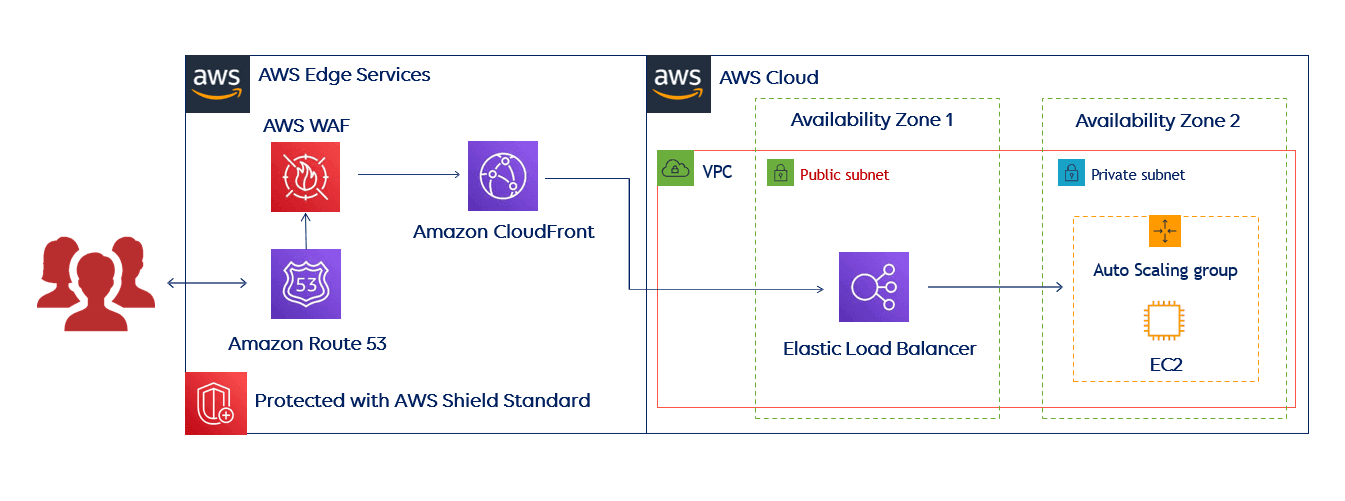
And here is an example of an architecture for those who use servers outside of AWS Cloud.

AWS Shield – service for the protection of 3 and 4 layer
At this point, it's clear that DDoS attacks are not going away. In fact, they're getting more powerful: AWS Shield Service mitigated a 2.3 terabit per second attack in February 2020.
AWS Shield and AWS WAF works well with Elastic Load Balancing, CloudFront CDN, and Amazon Route 53 DNS and protects your infrastructure from DDoS attacks of many types, shapes, and sizes.
There are two tiers of service:
AWS Shield Standard is available at no extra cost. It protects you from 96% of the most common attacks on 3 and 4 layers. This protection is applied automatically and transparently to your Elastic Load Balancers, Amazon CloudFront distributions, and AWS Route 53.
Benefits of AWS Shield Standard:
- DDoS protection: AWS Shield Standard inspects incoming traffic to your network and applies a combination of traffic signatures, anomaly algorithms, and other analysis techniques to detect malicious traffic. It sets some static thresholds for each of your resource types, but does not provide any custom protections.
- Visibility of attacks: You are provided with general information about DDoS attacks on the AWS network. You can find this information in the AWS Management Console in the Global threat dashboard.

AWS Shield Advanced. This paid service provides additional DDoS mitigation capability, intelligent attack detection, and mitigation against attacks at the application (AWS WAF included) and network layers. Price starts at $3000 per month.
Benefits of AWS Shield Advanced:
- Advanced real-time metrics and reports: You can always find information about the current status of your DDoS protection and you can also see the real-time report with AWS CloudWatch metrics and attack diagnostics.
- Cost protection for scaling: This helps you against bill spikes after a DDoS attack that can be created by scaling of your infrastructure in reaction to a DDoS attack.
- AWS WAF included: Mitigate complex application-layer attacks (layer 7) by setting up rules proactively in AWS WAF to automatically block bad traffic.
- You get 24×7 access to our DDoS Response Team (DRT) for help and custom mitigation techniques during attacks. To contact the DRT you will need the Enterprise or Business Support levels
AWS WAF – service for the protection of layer 7
AWS Web Application Firewall (WAF) helps against attacks on the application layer 7, such as SQL injection or cross-site scripting which attempts to abuse a weakness in your application. Due to the specific nature of these attacks, with AWS WAF you can easily create customized rules against malicious requests which could have characteristics like being disguised as good traffic or coming from bad IPs, unexpected geographies, etc.
As for other AWS services you pay only for what you use based on how many rules you deploy and how many web requests your web application receives, but you can look at our offer and get AWS WAF in one of our StormIT bundles.
You can read more about it in our blog post - What is a Web Application Firewall (WAF) and Why Use It? or watch the video below.
##### Specific features of AWS WAF:
- If the number of connections exceeds a threshold, this connection will receive 403 forbidden error responses.
- With WAF you can blacklist or whitelist requests using geographic restrictions from selected countries.
- You can block specific IP Addresses.
Amazon CloudFront DDoS protection
CloudFront CDN is one of the Edge Services and can be used as a “front door” to your applications and infrastructure, as the primary attack surface is moved away from critical content, data, code, and infrastructure. CloudFront DDoS protection is automatic and provided by AWS Shield Standard but can be also used with AWS WAF or Shield Advanced.
If you want to know more about CloudFront pricing, consider reading this article.
Amazon Route 53 DNS
Route 53 is a highly available and scalable cloud Domain Name System (DNS) AWS service. It is one of the Edge Services designed to give developers and businesses a reliable and cost-effective way to route end users to Internet applications. Route 53 is automatically protected by Shield Standard but can be also used with AWS WAF or Shield Advanced.
Amazon Elastic Load Balancing and AWS Auto Scaling
This is useful for those who use AWS resources as the origin for their applications. These two services can be used together to protect your resources and your infrastructure against traffic spikes because they can automatically scale-up and down the application infrastructure if needed.
Amazon Elastic Load Balancing distributes traffic automatically across multiple resources, such as EC2, DynamoDB tables, and Amazon Aurora Replicas.
AWS Auto Scaling monitors your applications and automatically adjusts resource capacity to maintain steady and predictable performance at the lowest possible cost.
How to get DDoS protection with third-party software solutions on AWS Marketplace?
There are more than 100 third-party Software as a Service (SaaS) solutions for DDoS protection on AWS Marketplace, but there are also offerings for Web Application Firewalls (WAFs) and other services.
If you are thinking about a third-party solution, it is worth looking into these three offerings – Citrix, F5, Fortinet.

Adam Novotny is an AWS Solutions Architect at Stormit with 5+ years of experience designing and optimizing AWS cloud architectures.
He supports customers across the full cloud lifecycle — from pre-sales consulting and solution design to AWS funding programs such as AWS Activate, Proof of Concept (PoC), and the Migration Acceleration Program (MAP).
Adam holds the AWS Certified Solutions Architect – Professional and AWS Certified CloudOps Engineer – Associate certifications.


