What is a Web Application Firewall (WAF) and Why Use it?
Understanding the difference between a traditional firewall and a Web Application Firewall (WAF) is essential for modern cybersecurity.
As businesses increasingly rely on web applications, WAFs have become crucial for defending against sophisticated DDoS attacks and application-layer threats. Layer 7 attacks now represent over half of all DDoS incidents on AWS, making enterprise-grade WAF protection essential for operational resilience.
This article delves into the specifics of WAF, what they protect against, and how AWS WAF can offer comprehensive protection for your web applications.
The difference between a firewall and web application firewall
The main difference between a firewall and a web application firewall (WAF) definition is that a firewall usually protects network and transport layers (layers 3 and 4). A WAF offers protection on the application layer (layer 7).
Traditional firewalls focus on volumetric and infrastructure attacks (SYN floods, UDP floods), while modern WAFs address sophisticated, behavior-mimicking attacks that appear legitimate. This distinction has become critical as attackers increasingly use AI and automation to craft precision-driven assaults at the application layer.
What is a web application firewall (WAF)?
A WAF monitors HTTP/HTTPS requests and protects these web applications from malicious activities on layer 7 of the OSI model. Hence, a WAF is a necessary protection against a growing number of web security threats.
Types of WAF
- Network-based (NWAF): Traditionally hardware-based in an on-premises environment.
- Host-based: WAF is implemented as an additional application or plugin on a web server.
- Cloud-based: WAF protection is transferred to an external cloud supplier. WAF is provided as part of the access network (DNS, CDN, or Load Balancer).
👉 In this article, you will mainly learn information about cloud-based WAFs.
What does WAF protect against?

A WAF should protect against the most common malicious web attacks, such as:
Common web application attacks and code injection techniques
SQL injection (SQLi): This can be done by entering a malicious code in SQL statements, via web page input (e.g. the user gives you an SQL statement that you will unknowingly run on your database). This malicious code can alter, steal or delete database data.
Cross-site scripting (XSS): A malicious script is injected into the code (e.g. HTTP, JavaScript, etc.) of a trusted website, allowing potentially sensitive user data such as cookies to be accessed. The code modified by this attack is not executed on the server but on the user's side.
Remote file inclusion (RFI): RFI is the process of embedding external files through vulnerabilities implemented in the web application. If the process allows modification of the path to a processed file (for example, if the path is included as a parameter), the attacker can use this path to input an external malicious file.
And more web application attacks and threats from the OWASP Top 10 publication.
DDoS attacks on layer 7 (HTTP Flood and Advanced Layer 7 Threats)
These are composed of requests (HTTP GETs and DNS queries are popular) that are designed to consume application resources (memory, CPU, bandwidth). An example is an attacker who continuously uses a website functionality (submitting a contact form or any API requests) that they know causes database and application processing so that the underlying web service is busy with malicious requests and can't deliver to other users anymore.
Modern Layer 7 DDoS attacks have evolved significantly. Attackers now employ "low and slow" tactics and horizontal attacks targeting multiple services simultaneously with encrypted HTTPS traffic that's difficult to inspect. These attacks mimic legitimate user behavior, making them harder to distinguish from real traffic. Read more in our article about DDoS protection.
Bad Bots and AI-Powered Threats
Bad bots are often programmed to do a variety of malicious jobs. They can try to break into user accounts, steal data, submit meaningless data through online forms, and perform other malicious activities. Bad bot activity is most often manifested by an abnormal increase or decrease in visits in unusual periods with a high rate of immediate leave (bounce).
With AWS WAF's Web Bot Authentication (WBA), you can cryptographically verify legitimate AI bots and agents while blocking malicious bot traffic with unprecedented accuracy.
Benefits of WAF
- Completes other protective systems such as firewalls and intrusion prevention systems.
- Lower costs for cloud security by avoiding the need for expensive dedicated hardware or IT security staff.
- Filters and monitors traffic on the application layer (layer 7) which is not possible with any other type of firewall.
- Prevents unauthorized transfer of sensitive data away from the application.
- Reduce the risk of downtime, data theft and security breaches.
- WAF can be scaled to protect against the largest DDoS attacks on layer 7.
- Provides visibility through integrated logging and real-time monitoring dashboards.
- Automated threat response with minimal operational overhead.
How does a WAF work?
A WAF is usually placed logically between users and web servers and analyzes and compares network traffic with the vulnerability database. A WAF creates a set of rules designed to protect your website and detects unwanted traffic. It usually blocks this traffic but can be set up to only monitor it.
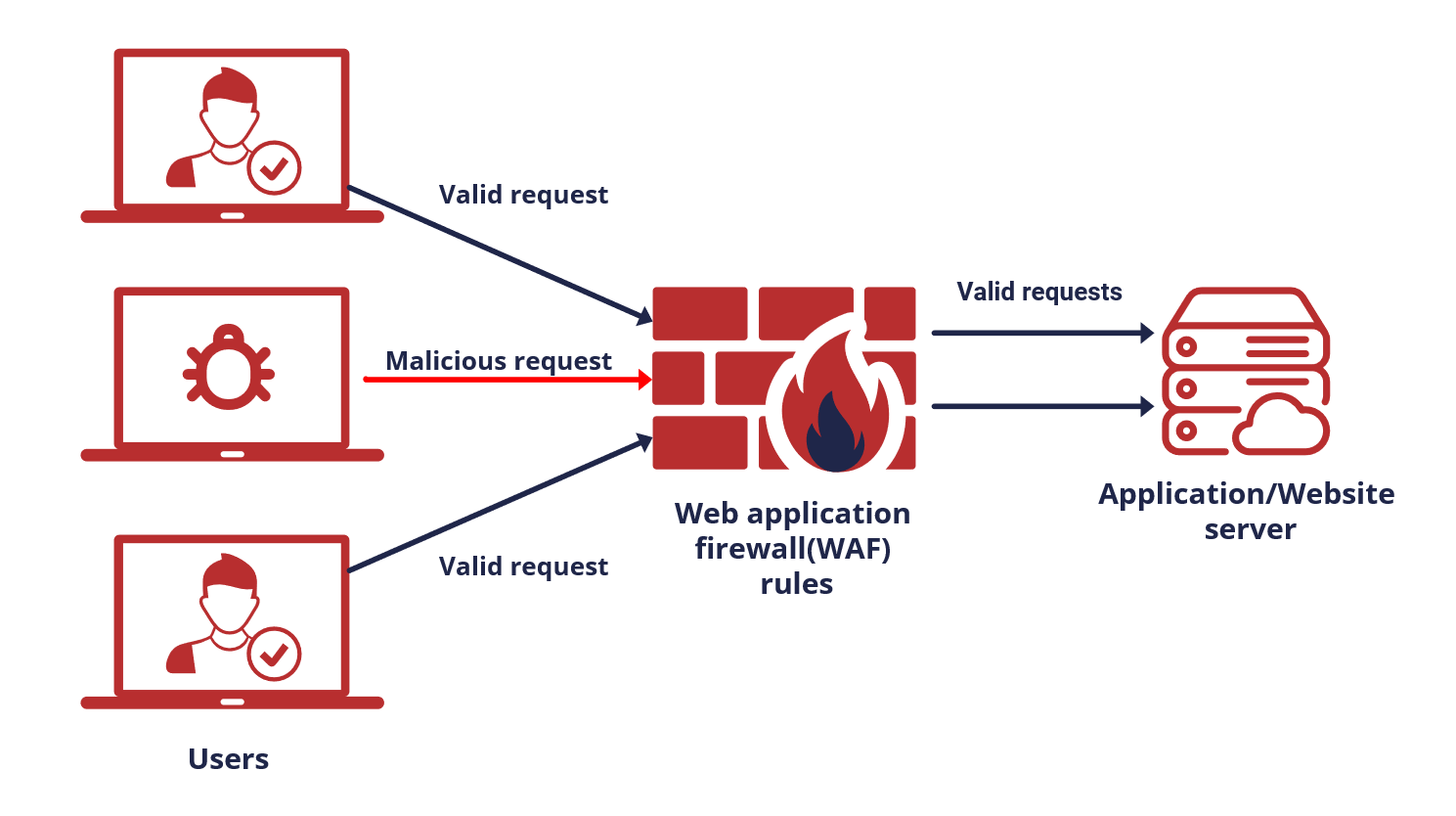
Modern WAFs now employ machine learning and behavioral analysis to understand your traffic patterns within 15 minutes of activation, enabling rapid threat detection and mitigation within seconds rather than hours.
Want to find out how a WAF can help your particular use case?
Talk to a WAF specialist
AWS Web Application Firewall(AWS WAF)
The AWS WAF is a cloud-based solution that helps prevent attacks on the application layer 7 and a great web application firewall example. Due to the specific nature of these attacks, with an AWS WAF you can easily create customized rules against malicious requests which could have characteristics like being disguised as good traffic or coming from bad IPs, unexpected geographies, etc.
AWS WAF protection is tightly integrated with AWS services that AWS customers use to deliver content such as Amazon CloudFront CDN, the Application Load Balancer (ALB), and the Amazon API Gateway. But AWS WAF can be also used for the protection of services from other providers, but your content has to be served through the CloudFront distribution network.
How does an AWS WAF work?
You use an AWS WAF to control how an Amazon CloudFront distribution, an Amazon API Gateway, an Application Load Balancer or an AWS AppSync GraphQL API responds to web requests.

What can an AWS WAF do?
- Blocking of malicious traffic: SQL injection (SQLi), Cross-site scripting (XSS), Remote file inclusion (RFI), DDoS attacks on layer 7, Bad bots based on applied rules.
- Intelligent Layer 7 DDoS Protection: AWS WAF AntiDDoS Managed Rule Group detects and mitigates HTTP floods within seconds using AI-powered traffic pattern analysis.
- Traffic filtering: Rate-based rules, IP and geographical filtering, Actions on HTTP/HTTPS traffic (allow/block/challenge), Regex and String match support.
- Bot Management: Web Bot Authentication (WBA) cryptographic verification for legitimate AI bots and agents with automatic allowlisting.
- Monitoring: Amazon CloudWatch metrics/alarms, sampled logs, and real-time Sankey visualization dashboard showing traffic flow and rule interactions.
- Automated Recommendations: AWS WAF provides real-time security recommendations and threat detection activity visualization.
Modern AWS WAF Capabilities
Redesigned Console Experience
The updated AWS WAF console delivers:
- Pre-configured Rule Packs: Select your application type and receive automatically customized protection parameters.
- Streamlined Workflow: Deployment time reduced significantly with visual rule builders.
- Integrated Log Explorer: Real-time security monitoring with Sankey visualization for rule interaction patterns.
- Outcome-driven Dashboard: Consolidated threat detection metrics, rule performance analytics, and actionable insights in a single view.
- Automated Security Recommendations: Real-time suggestions based on your traffic patterns and threats.
Application Layer DDoS Protection (AntiDDoS)
AWS WAF now includes built-in Layer 7 DDoS protection:
- Automatic Traffic Baseline: Establishes normal traffic patterns through machine learning analysis.
- Rapid Threat Detection: Detects and mitigates application-layer attacks within seconds of launch.
- Flexible Mitigation Actions: Challenge (silent browser verification) or Block options based on suspicion levels.
- Reduced False Positives: Advanced algorithms distinguish malicious traffic from legitimate usage spikes.
Web Bot Authentication (WBA)
Cryptographic bot verification framework for enterprise environments:
- AI Bot Verification: Automatic allowlisting of verified bots including Bedrock Agent Core agents and legitimate crawlers.
- Enhanced Bot Identification: Vendor, name, account labels, and coordinated activity detection.
- Session and Token Tracking: Advanced fingerprinting for bot activity patterns.
Types of rules
Before choosing the right type of security rules, you should understand what vulnerabilities your web application has. If you need help finding this out, contact us for a consultation.
1. AWS Managed rules
You can select from a variety of AWS managed rule groups to protect your application from multiple threats. These rules are written by security experts who have extensive and up-to-date knowledge of threats and vulnerabilities. Managed rules are continuously updated to protect against emerging threats.
These managed rules include:
- Use case specific rules for protection based on your web application characteristics, such as the application OS or database type.
- Rule groups that can help you mitigate common threats in the OWASP Top 10 publication.
- An IP reputation list acquired from AWS threat intelligence team to block known malicious IPs.
- Layer 7 DDoS AntiDDoS protection and Web Bot Authentication (WBA) for cryptographic bot verification.
2. Custom rules
You can write custom rules specific to your web application/database to block undesired patterns in parts of the HTTP/HTTPS request, such as headers, method, query string, URI, body and IP address. These custom rules can be used together with AWS Managed Rules.
3. AWS Marketplace Rules
You can also find rules created by security vendors that have built their own rule sets on AWS WAF on the AWS Marketplace. AWS WAF now features a dedicated Marketplace page for direct deployment of partner solutions.
4. Advanced Automated Mitigations
AWS provides the AWS WAF Security Automations Solution which automatically deploys a set of AWS WAF rules that filter common web-based attacks, but also provide advanced log analysis. This automated solution leverages AWS WAF's APIs to react to threats detected from logs, honeypot URLs, and more to automatically update rules and block malicious IP addresses. An example of this is shown below.

Benefits of AWS WAF
Easy to deploy
If you are already using services like Amazon CloudFront or Application Load Balancer, you can be up and running with an AWS WAF within a few minutes. And you don't have to re-architect your whole network infrastructure when starting with an AWS WAF, which is sometimes necessary for WAFs from other providers. There is also no additional software to deploy, any DNS configuration or SSL/TLS certificate to manage. With pre-configured rule packs, security configuration is automatically customized based on your application type, eliminating complex manual setup.
Affordable
Like other AWS services, you pay only for what you use, based on the number of rules you deploy and the volume of web requests your application receives. To optimize costs, it's crucial to limit AWS WAF monitoring to only the parts of your application or website where it's truly needed. With bundled service offerings, you can combine CDN, WAF, Route53, and CloudWatch into transparent, predictable pricing tiers.
Managed service and rules
The AWS WAF is a fully managed service, so you don't have to worry about scaling and updates/patches. With Managed Rules for your AWS WAF, you can quickly get started and protect your web application or APIs against common threats. Managed rules are automatically updated so you can spend more time building applications.
Comprehensive security with Well-Architected review
The Stormit team helps organizations protect their websites and applications against all commonly known attacks and exploits by leveraging the protection of AWS Services, such as AWS WAF and AWS Shield. Thanks to the free AWS Well-Architected review, it's easy to understand how to integrate these services into your architecture.
This reference architecture below includes several AWS Edge Services that the Stormit team recommends using because it can help you improve your web application's resiliency against known web application attacks, but also secure your application and infrastructure in other ways. This architecture is intended for those who use only AWS services.
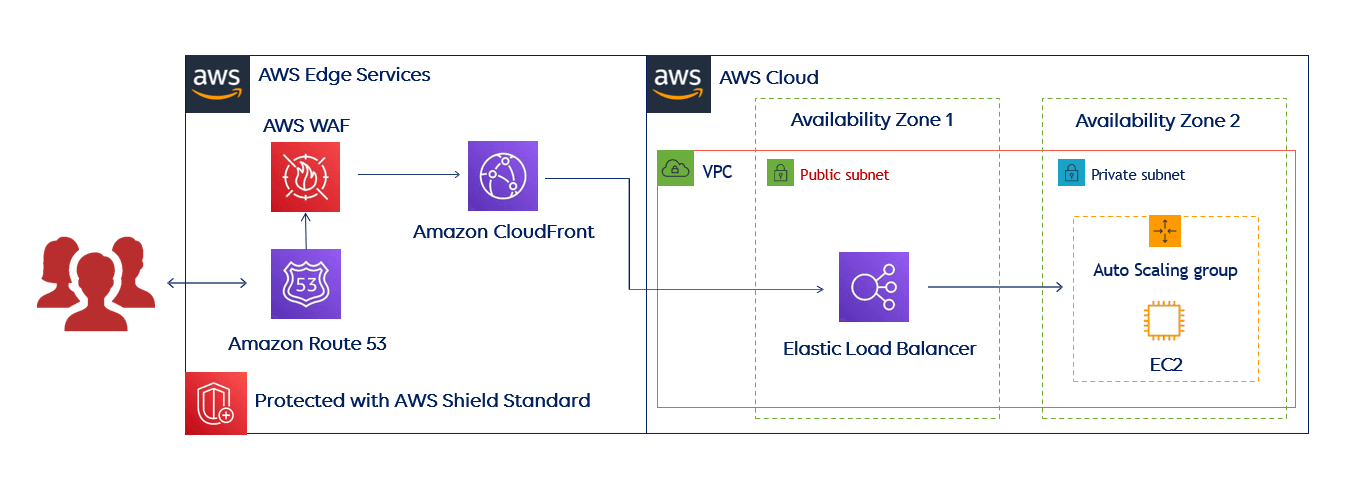
Here is an example of Stormit's recommended architecture for those who use servers outside of the AWS Cloud.

Current Threat Landscape
Layer 7 attacks now represent a significant portion of DDoS incidents on AWS. Attackers increasingly employ:
- AI-Powered Precision Attacks: Machine learning optimizes attack patterns to mimic legitimate traffic.
- Low and Slow Tactics: Gradually exhaust resources rather than volumetric floods.
- Horizontal DDoS: Target multiple IPs and services simultaneously.
- Encrypted Attack Traffic: HTTPS-based attacks bypass traditional inspection.
Modern WAF solutions must combine traffic pattern analysis, behavioral biometrics, and automated response to detect and mitigate these sophisticated threats in real time.
We offer a free AWS Well-Architected review to evaluate your architecture and guide you in following AWS best practices. Our consultation includes AWS Edge Services like Amazon CloudFront, AWS WAF, Amazon Route 53, and AWS Shield to enhance your application's security.
An AWS Solutions Architect with over 5 years of experience in designing, assessing, and optimizing AWS cloud architectures. At Stormit, he supports customers across the full cloud lifecycle — from pre-sales consulting and solution design to AWS funding programs such as AWS Activate, Proof of Concept (PoC), and the Migration Acceleration Program (MAP).


