What are AWS-managed Prefix Lists and How do you Use Them?
In this article, you will learn:
- What is an AWS-managed Prefix List?
- AWS-managed prefix list with Amazon CloudFront Ips
- How do you use the CloudFront-managed prefix list
AWS (Amazon Web Services) recently announced the availability of AWS-managed Prefix Lists for Amazon CloudFront. As a result, AWS customers can now restrict inbound HTTP/HTTPS traffic to AWS VPCs from IP addresses belonging to CloudFront servers.
In this blog post, we'll learn what managed prefix lists are, how they can help protect your AWS infrastructure, and how they work with CloudFront, Application Load Balancers, and Auto-Scaling groups of Amazon EC2 instances.
If you want to know more or watch how to implement CloudFront managed prefix list to VPC security group. Watch the video below.
What is an AWS-managed Prefix List?
AWS-managed prefix lists are created and maintained by AWS and are available to anyone with an AWS account. A prefix list is a collection of one or more IP CIDR blocks used to simplify the configuration and management of security groups and routing tables.
There are customer-managed prefix lists and AWS-managed prefix lists. This blog post focuses on AWS-managed prefix lists for Amazon CloudFront.
You can simply find them in AWS Management Console, under VPC, Managed prefix lists.

AWS-managed lists include updated IP addresses of AWS services which you can add to security groups or route tables to better manage what service or who can reach your VPC.
The following AWS-managed prefix lists are available:
- Amazon S3: com.amazonaws.region.s3
- Amazon DynamoDB: com.amazonaws.region.dynamodb
- Amazon CloudFront: com.amazonaws.global.cloudfront.origin-facing
AWS managed prefix list with Amazon CloudFront IPs
You can use the AWS-managed prefix list for Amazon CloudFront. AWS keeps the managed prefix list up-to-date with the IP addresses of CloudFront’s edge servers, so you no longer have to maintain a prefix list yourself with, for example, this solution: Automatically update your security groups by using AWS Lambda.
Until recently, when using a load balancer or similar endpoint as the origin for a CloudFront distribution, you had to allow incoming HTTPS/HTTP traffic from anywhere (0.0.0.0/0). So your ALBs and EC2 instances behind it were accessible for anybody and this could be abused via a DDoS attack.
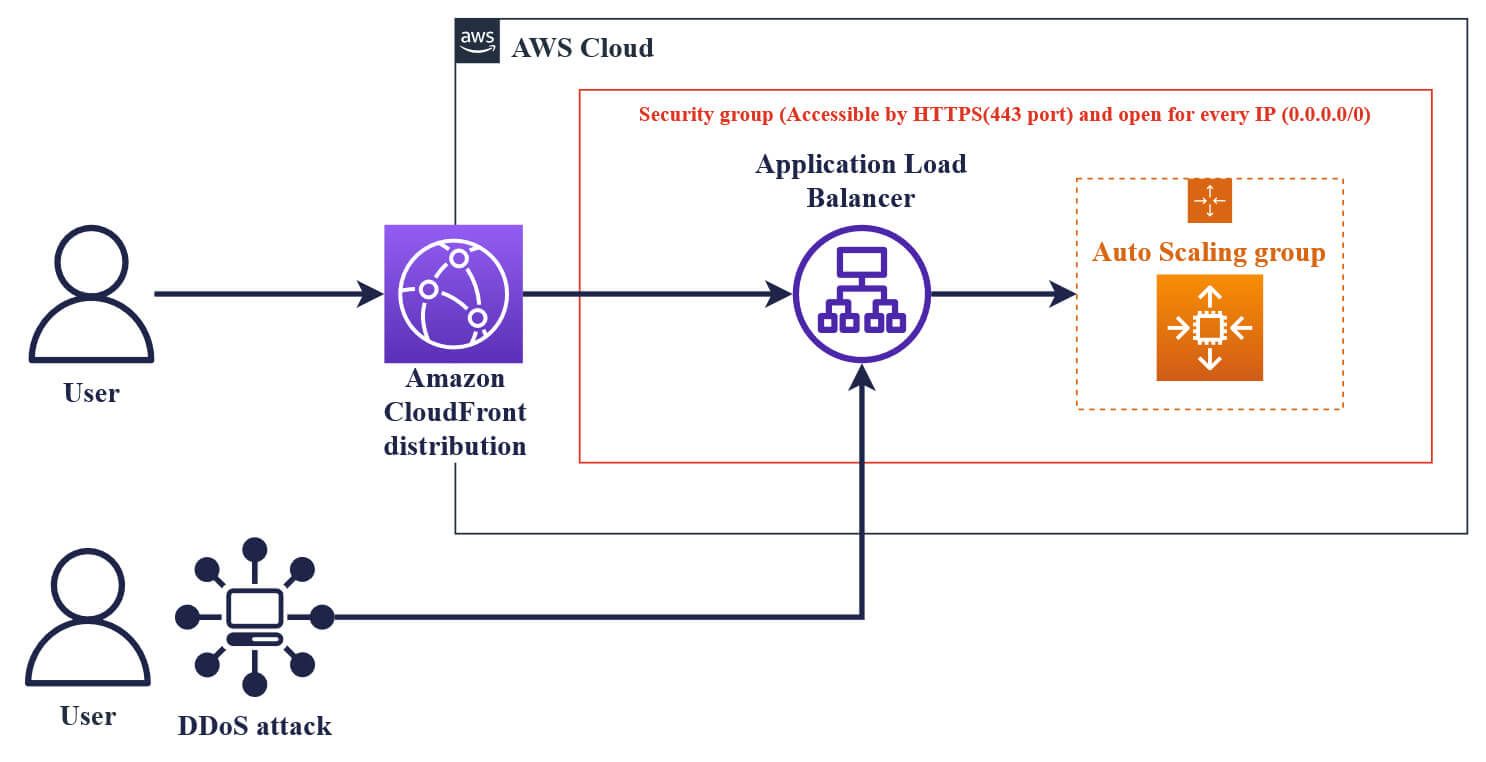
This AWS architecture with EC2 instances, ALB and CloudFront is widely used for dynamic content, if you want to know more about it, try reading our blog post: Creating a CloudFront Distribution for Amazon EC2 and ALB
Now, you can use the AWS-managed prefix list for CloudFront in the inbound rules of your VPC security group, allowing only CloudFront IP addresses to access your EC2 instances. Your infrastructure will then only be accessible through CloudFront distribution.

However, keep in mind that anyone can create a CloudFront distribution. So, this does not guarantee that all the requests arriving at your load balancer originate from your CloudFront distribution.
How do you use the CloudFront-managed prefix list?
The managed prefix list is available for use via the AWS Console and the AWS SDK. The prefix list can be referenced in your CloudFormation templates in the available regions. There is no additional fee for using the CloudFront-managed prefix lists.
The Amazon CloudFront-managed prefix list weight is unique in how it affects Amazon VPC quotas:
- It counts as 55 rules in a security group. The default quota is 60 rules, leaving room for five additional rules. However, you can request a quota increase.
- It counts as 55 routes in a route table. The default quota is 50 routes, so you must request a quota increase.
For example, you can create a security group rule that allows inbound HTTPS access only from the CloudFront-managed prefix list. If you remove all other inbound rules from the security group, you prevent any non-CloudFront traffic from reaching the instance.

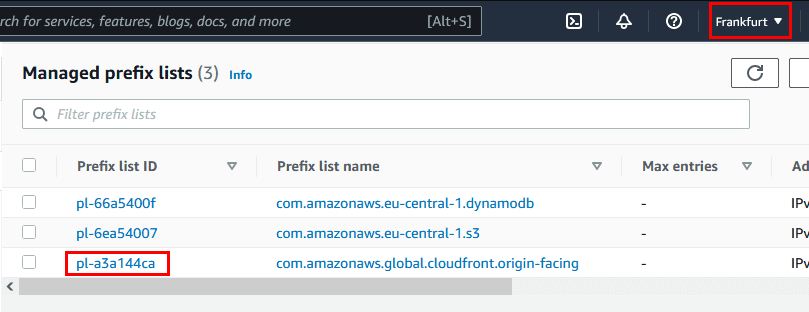
If you need to find the Prefix list ID of a region-specific CloudFront-managed prefix list, try looking into the VPC Console and choosing the desired region.
Conclusion
An AWS-managed prefix list, especially for CloudFront, simplifies security in your infrastructure. We believe that this function is useful for a lot of current AWS customers and our certified AWS Solution Architects can help you set it up.
