AWS Organizations: How to Manage Multiple AWS Accounts?
When your AWS (Amazon Web Services) environment gets to the stage where you need to add new user accounts and manage multiple of them, you will need to find a way to do this in the simplest way possible. Adding permissions that give these users access to the right resources in the AWS Cloud is also potentially difficult. This is where AWS Organizations comes in.
In this blog post, we will look at what AWS Organizations is, its components, features and benefits, as well as the main difference between AWS Identity and Access Management (IAM) and AWS Organizations.
What is AWS Organizations?
AWS Organizations is an account management service that allows you to consolidate multiple AWS accounts into a single organization that you create and centrally manage. AWS Organizations includes account management and consolidated billing capabilities to help you better meet your organization's budget, security and compliance needs.

As an administrator of an organization, you can create and close AWS accounts in the organization and invite existing accounts to join the organization. It also offers a more flexible hierarchy of your AWS accounts and resource groups in the form of organizational units (OUs).
AWS Organizations is a global service with a single endpoint for all AWS Regions. You don't have to explicitly select a region.
AWS Organizations components and architecture
For the right understanding of what AWS Organizations can do, it’s best to understand what components and what architecture it provides for your accounts and groups.
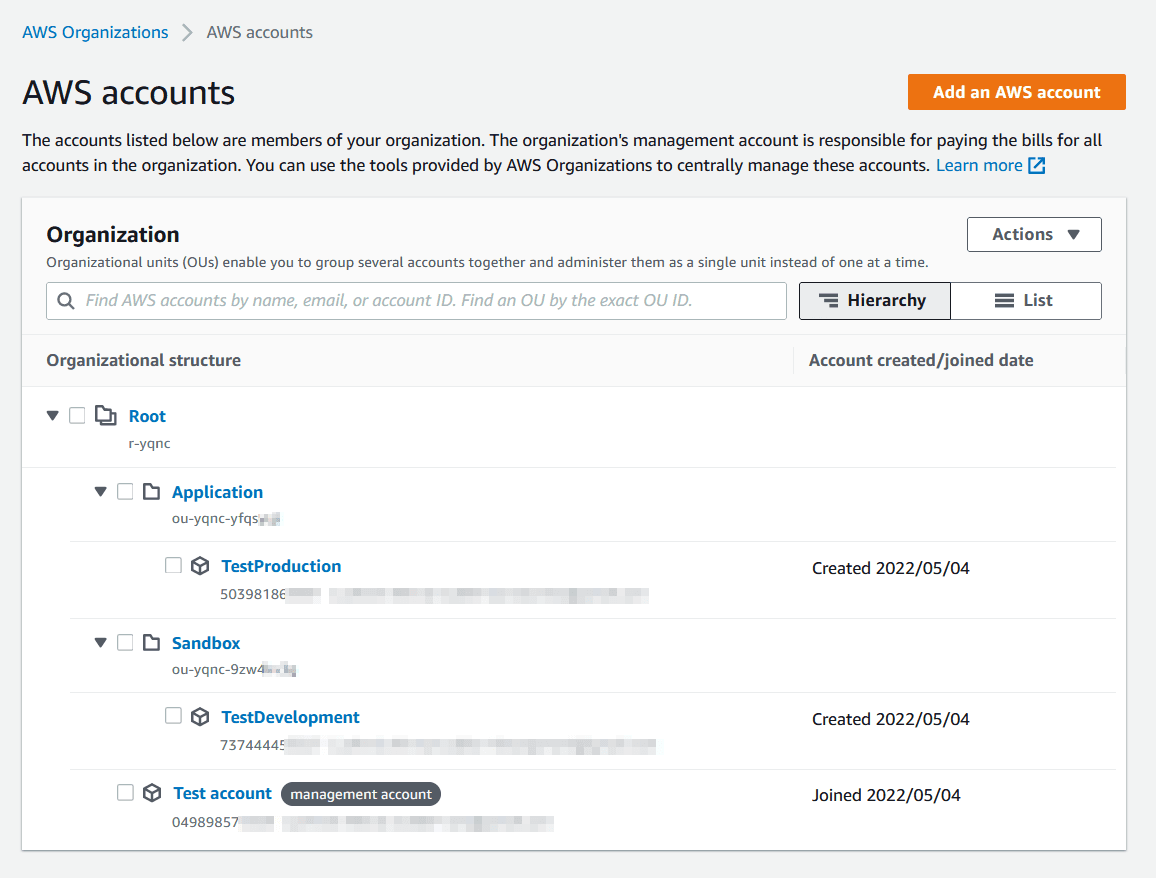
Below you can find a simple example of an AWS Organizations hierarchy.

Let’s look at every part of this hierarchy on a more thorough level.
Management account
This is the AWS account that you use to create your organization. From the organization's management account, you can do the following:
- Create and close accounts in the organization
- Manage invitations and invite other existing AWS accounts to your organization
- Remove accounts from the organization
- Apply policies to entities in your organization (roots, OUs, or accounts)
- Enable integration with other supported AWS services
The management account has the responsibilities of a payer account and is responsible for paying all charges that are accrued by the member accounts.
Member Account(s)
These AWS accounts make up all of the rest of the accounts in an organization.
A member account can be a member of only one organization at a time.
You can attach a policy to an account to apply controls to only that account.
- A New AWS account can be directly added to the organization.
- Existing AWS accounts can be added (invited) to the organization.
Organizational Unit (OU)
- An organizational unit is a group of AWS accounts within an organization.
- An OU can also contain other OUs enabling you to create a hierarchy. This enables them to reflect the company’s structure.
- One account cannot be added under two different OUs.
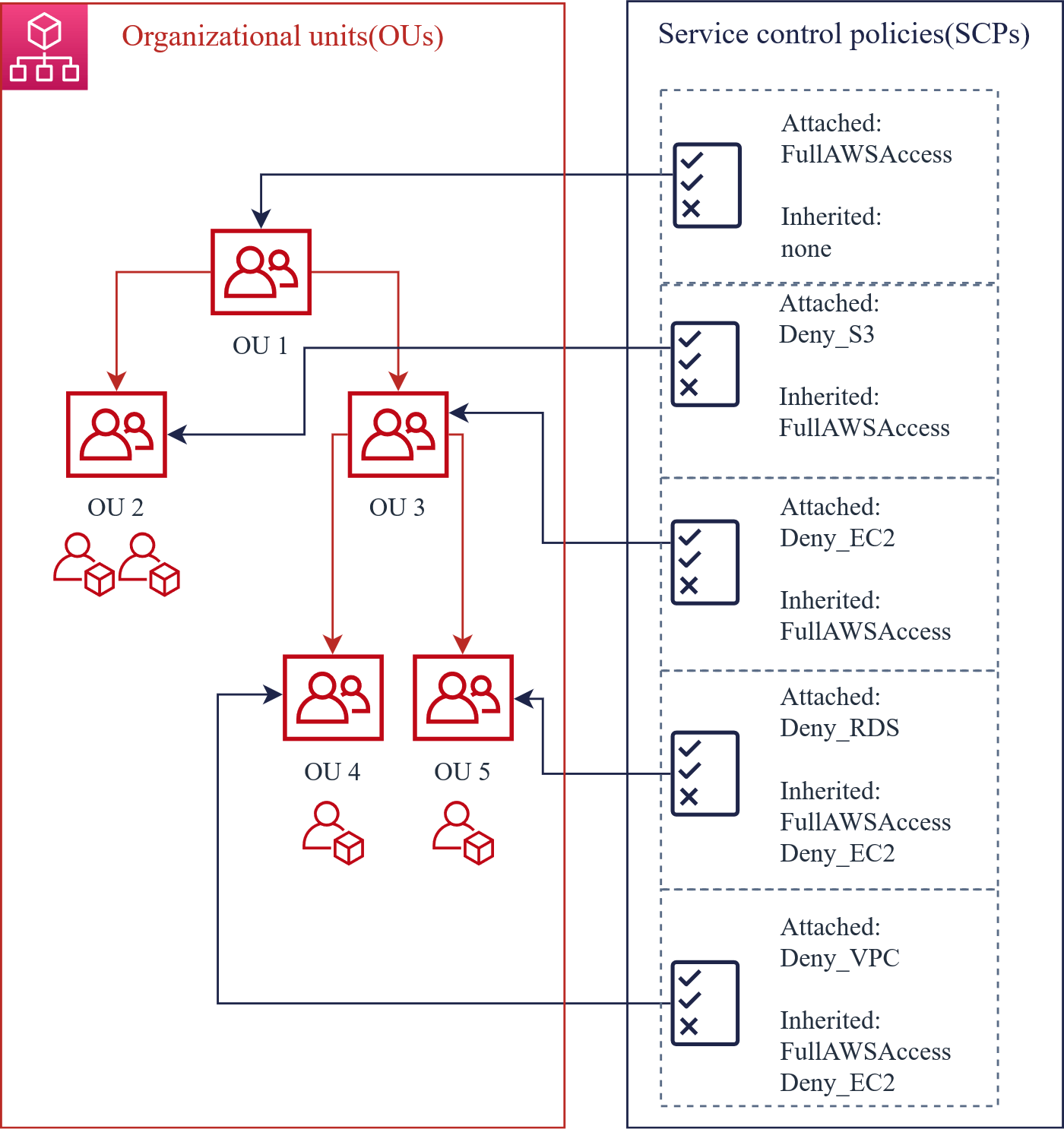
Service Control Policy (SCP)
- Service Control Policy (SCP) is a document that describes controls to be attached to the entire organization, OUs, or individual AWS accounts.
- The policy defines the services and actions that users or a role can perform.
- Policies are inherited through hierarchical connections in an organization.
AWS Organizations features
AWS Organizations has two available feature sets:
- Consolidated Billing features: All organizations support this subset of features, which provides basic billing management tools.
- All features: This feature set is the preferred way to work with AWS Organizations, and it includes Consolidating Billing features. When you create an organization, enabling all features is the default.
Consolidated Billing
You can use this feature of AWS Organizations to consolidate billing and payment for multiple AWS accounts. Every organization in AWS Organizations has a management account that pays the charges of all the member accounts.
Consolidated billing has the following benefits:
- One bill – You get one bill for multiple accounts.
- Easy tracking – You can track the charges across multiple accounts and download the combined cost and usage data.
- Combined usage – You can combine the usage across all accounts in the organisation to share the volume pricing discounts, Reserved Instance discounts and Savings Plans.
An AWS Organization can be upgraded to using all features at any time, but to do so each member account must approve of the change.
All Features of AWS Organizations
If your organisation has all features enabled, you can access the advanced central governance and management capabilities in AWS Organizations.
AWS Organizations offers the following features:
- Manage multiple AWS accounts: You can create groups of accounts and then apply policies to those groups and establish boundaries that define the policies, services and resources used by them.
- Control access and permissions: Enforce policies across users based on teams, business divisions and projects.
- Share resources: You can share that service across multiple users, both within and beyond the same AWS organisation.
- Use for free: Activating this feature is free. The accounts are only charged for the AWS services and resources they consume.
Service Control Policy (SCP)
This type of policy determines which services and actions are available to users (or roles) for specified accounts. Note that SCPs do not grant permissions; they instead act as a filter. This means that the accounts, users and roles must already have these IAM permissions available.
Tag Policy
AWS tags are powerful because they are user-defined and flexible. However, they also create mistakes. This type of policy enforces tag standardisation across accounts in your organisation.
For more information, see Tag policies
Policies that configure automatic backups for the resources in your organisation's accounts
You can use backup policies to configure and automatically apply AWS Backup plans to resources across all your organization's accounts. For more information, see Backup policies
Integration with other AWS services
You can leverage the multi-account management services available in AWS Organizations with selected AWS services. For a list of services and the benefits of using each service, see AWS services that support AWS Organizations.
AWS Organizations use cases
- Automate the creation of AWS accounts and categorize workloads using groups: for example, you can create separate groups to categorize development and production accounts.
- Implement and enforce audit and compliance policies: You can apply SCPs to ensure that users in your accounts only perform actions that meet your security requirements.
- Provide tools and access for your security: You can use AWS Organizations to create a Security OU and provide them with read-only access to all of your resources.
- Share common resources across accounts: AWS Organizations makes it easy for you to share critical central resources across your accounts. For example, you can share your central AWS Directory Service Managed Microsoft Active Directory. Or you could use AWS Service Catalog to share IT services hosted in designated. Additionally, you can ensure application resources are shared across your organization using AWS Resource Access Manager.
Achieve unrivaled security and compliance with the StormIT Cloud Check-Up. We perform a gap analysis with more than 600 Best Practice Checks to reduce risk, identify security vulnerabilities, and remediate compliance breaks in your AWS environment.
AWS Organizations pricing
AWS Organizations is a feature of your AWS account offered at no additional charge. Therefore, basically every feature described in this article is for free and you can use it on any scale with as many accounts as your organization needs.
What are the benefits of AWS Organizations?
- Quick and precise permission administration: AWS accounts can be allocated to teams, workloads, or products. Separate accounts can provide custom environments and accommodate the differing security needs for each team.
- Apply boundaries: Different projects within the organization may be exposed to different security and compliance requirements. You can easily enforce unique identity policies.
- Contain damage within logically isolated user accounts. If a specific user account is compromised, only the resources assigned to that AWS Organizations' user account will be exposed to the higher risk.
- Easily managed billing: The use of multiple accounts simplifies how you allocate AWS costs. You can use them to identify which projects or services are responsible for AWS charges.
AWS Organizations vs AWS IAM
AWS organizations, especially SCPs, do not replace associating IAM policies with AWS accounts, groups and roles. AWS Organizations don’t work without AWS IAM, but if you have simple AWS infrastructure, you don’t need to use AWS Organizations.
IAM policies are used for AWS accounts to allow or deny them access to AWS services such as Amazon EC2 and Amazon S3, and specific AWS resources (such as selected S3 buckets) or API operations (such as S3) to create buckets.

IAM users are a great way to manage employee access as one AWS account can have multiple IAM users and each can have their own permissions.

IAM roles are used to authenticate service accounts. For example, if you're running the AWS CLI on an Amazon EC2 instance and want to permit it to manage an Amazon S3 bucket, you can use an IAM role to do so so you don't have to leave your credentials on the remote server.

However, with AWS Organizations, you can use SCPs to allow or deny access to specific AWS services for individual AWS accounts or groups of accounts in an OU. The specified action of the attached SCP affects all IAM users, groups and roles of the AWS account, including the root account identity.
Which one should you use?
The answer is basically both: IAM users and AWS Organizations do different things, but use Organizations only if you need it.
- Separate your infrastructure: Use AWS Organizations and create separate accounts for development and production.
- You may also want to create two more environments: testing, which contains clean dummy data and staging, and a full production environment to capture any possible occurrences before they affect real customers/users.
- Create multiple IAM users with proper policies applied in the development environment to provide managed access to your employees.
- Production should only be updated by authorised personnel, including of course the IAM service accounts required for normal operation.
Conclusion
AWS Organizations brings capabilities that help you reach your business goals around budget, security and compliance in complex AWS environments. This blog post should help you understand the basics of this service and decide if it is the right solution for you.
Adam Novotny is an AWS Solutions Architect at Stormit with 5+ years of experience designing and optimizing AWS cloud architectures.
He supports customers across the full cloud lifecycle — from pre-sales consulting and solution design to AWS funding programs such as AWS Activate, Proof of Concept (PoC), and the Migration Acceleration Program (MAP).
Adam holds the AWS Certified Solutions Architect – Professional and AWS Certified CloudOps Engineer – Associate certifications.


